Definition
Related Definitions
Phishing
What is Phishing?
Phishing is a technique based on social engineering often used by miscreants or fraudsters for nefarious reasons such as stealing user data such as credit card details and other credentials. It usually happens when an attacker pretending as a trusted source cheats a user into opening a text message or an email. The user is then duped into clicking a malicious link that leads to the installation of malware (malicious software), revealing the user's sensitive information or freezing the device due to the ransomware attack. Unauthorized purchases, identity theft, and money theft are just some of the consequences of such an attack.
Many a time, to represent themselves as someone belonging to a legitimate firm, scammers often create fraudulent websites to dupe the victims. These websites are similar to official websites and thus prompt users to believe them as an authentic source.
Visitors who land on these fraudulent websites created by the fraudsters submit their crucial personal information such as social security numbers, passwords, account numbers, and login IDs under the impression that they interact with genuine business people. Instead, the information thus submitted is used by scammers to either steal the visitor's funds, identity, or both, and this information is shared with other criminal parties in exchange for money. Phishing is a data theft where the visitors unknowingly volunteer to share their details with a person with malicious intent.
Summary
- Phishing is a technique based on social engineering often used by miscreants or fraudsters for nefarious reasons such as stealing user data such as credit card details and other credentials.
- Many a time, to represent themselves as someone belonging to a legitimate firm, scammers often create fraudulent websites to dupe the victims.
- Visitors who land on these fraudulent websites created by the fraudsters submit their crucial personal information such as social security numbers, passwords, account numbers, and login IDs
Frequently Asked Questions
How do phishing scammers convince victims to share their vital personal information?
Phishing scammers target the victims by creating a false sense of security by tricking or replicating the common, esteemed logos of popular, legal companies or masquerading to be victims' kin. Usually, the scammers try to convince victims they need personal information instantly, or the victim will face severe consequences, such as suspended accounts or personal damage.

Image Source: © Carlosbcna | Megapixl.com
A perfect example of phishing is an identity thief establishing a website that resembles looks like that of a central bank. Later, the scammer sends emails claiming to be from some well-known bank and requesting the mail recipients to enter their personal banking information (such as their PIN) into the website to refurbish their bank records. And thus, once the scammer gets the required personal information, they attempt to access the victim's bank account.
Phishing scams are some of the most prevalent attacks on users. As per the Federal Bureau of Investigation (FBI), over 1,14,700 people fell into the trap of phishing scams in 2019. Overall, these victims lost $57.8 million, which amounted to $500 each.
What are the few ways to save yourself from phishing attacks?
- Exceptional big deals or offers. If an email tout offers too good to be real, beware! For instance, an email declaring that you have won a prize worth millions or billions of dollars may be enticing you to get you to click a link or transfer crucial personal information.
- Anonymous or unfamiliar senders. Though phishing emails may appear like they are sent by someone familiar to you, however, if anything seems unordinary, be careful. If in doubt, hover over the sender's email address to ensure that the email address is similar to your expected email address. Make a phone call and contact the company if you are doubtful of an email or website. One should never answer emails with any personal details.
- Hyperlinks and attachments. These are particularly worrying if received from an anonymous sender. One should not open the links or attachments unless they are sure they are from a secure sender.
- Wrong spelling in the web address. Phishing sites commonly use web addresses that look identical to reliable sites but have a wrong spelling, like substituting a "1" for an "l."
- Instant pop-ups. Be careful of websites that instantly display pop-up windows, particularly those requesting your username and password. Resort to two-factor authentication, browser with anti-phishing detection, and regularly update security on your systems.

Image Source: © Dwnld777 | Megapixl.com
What kind of phishing emails and text messages do the spammers send to the victims to lure them?
As per the Federal Trade Commission (FTC), to deceive users into clicking on a link or opening an attachment, phishing emails and text messages often narrate stories. For instance, phishing attempts can:
- Claim that they have observed suspicious activity like login attempts on your account.
- Say that there is an issue with your account or with the payment information
- Tell you that you need to confirm or refurbish personal information
- Contain a fake invoice
- You may be asked to click on a link to make a payment
- Claim that you are qualified to sign up for a government refund
- Can offer a token for free goods or services
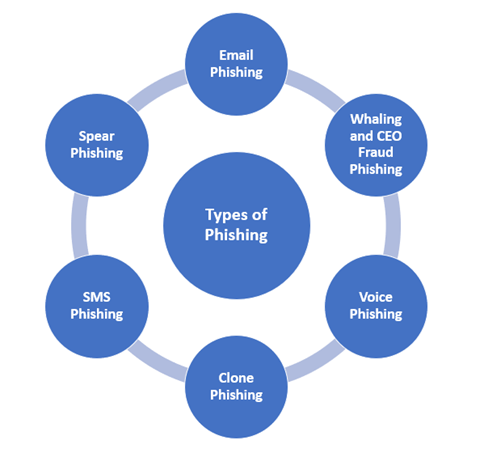
What are the different types of phishing methods used by spammers to extract the victims' personal information?
Email phishing
Usually, when phishing messages are not personalised or targeted to a specific group or company, they are delivered via email. This is termed "bulk" phishing. The bulk phishing message content varies widely based on the aim of the spammer. Typical targets for impersonation include banks and financial institutions, email and cloud productivity providers, and streaming services.
Spear phishing
In spear phishing involves a spammer target explicitly a particular individual or organisation with tailored phishing emails. Unlike bulk phishing, spear phishing attackers usually collect and use personal information about their target to increase their chances of success in the attack. Executives or those who work in financial departments and have access to an organisation's sensitive financial data and services often become the victims of spear phishing. A 2019 study had revealed that accountancy and audit firms are frequently the targets for spear phishing.
Fancy Bear, a Russian cyberespionage group, used spear-phishing attacks to target email accounts associated with Hillary Clinton's 2016 presidential campaign. In the process, over 1,800 Google accounts were attacked by the spammers.
Source: Copyright © 2021 Kalkine Media
Whaling and CEO fraud
In whaling, phishing attacks are carried out against senior executives and other high-profile targets. The content is specifically designed to match the interest of the person who is to be targeted. Contrarily, CEO fraud is just the opposite of whaling. CEO fraud involves creating spoofed emails purportedly from senior executives to get other employees at an organisation perform a desirable action.
Clone phishing
Clone phishing refers to a phishing attack through which a legitimate and earlier delivered email carrying an attachment/link has had its content and receiver address or addresses taken and used to create an almost same or cloned email.
Other Phishing methods include – Voice phishing, SMS phishing, and Page hijacking. Voice phishing refers to the use of telephony to carry out phishing attacks. The spammers dial a large set of telephone numbers and play automated recordings wherein they make wrong claims of suspicious activity on the victim's bank accounts or credit cards.
SMS phishing is conceptually identical to email phishing, except that the spammers use cell phone text messages to deliver the "enticement" in this method. Page hijacking requires compromising authorised web pages to redirect users to a malicious website through cross-site scripting.
